
And now for something completely different: how to quickly and easily improve the security of your online accounts. (Spoiler alert: use two-step verification.)
(The problem with) passwords
We commonly use passwords to log on to our various online accounts. That password is how we verify to the site that we are, in fact, who we say we are. (I.e. us.) From a security point of view, that one little password is the only thing stopping others from pretending to be us. And passwords have their faults.
To avoid people guessing our password we should use strong passwords. Which, admittedly, is a huge pain in the backside, so we don’t always do that. And even if we do, our passwords can still end up in the wrong hands as the result of a data breach. But wait – it gets worse. If someone hacks your email, they can take over any other online account you have by using the “forgot your password?” link and having the password reset. (Unless you use two-step verification on that account. Which, conveniently enough, is what this article is about.)
One way of improving our security is by requiring one or more additional verification steps (in addition to our password) before we can log in to a site. That way, even if someone manages to get hold of (or guess) our password, they still wouldn’t be able to log in to our account, since the password would only be one of several required steps of verification.
As an example of two-step verification that most of use are likely to be familiar with, think of withdrawing money from an ATM. First off, you need the physical card. One step. But then you also need an additional form of verification, commonly a PIN number (but soon it could also be your fingerprint).
Two-step verification in practice: one small step for you, one giant(ish) leap for your security
One of the most common ways of implementing two-step verification in practice is through text messages. The way it works is that once you have entered your password you will be sent a text message with an additional string of numbers and/or letters to enter. The benefit here is that in order to break into your account, someone would need access to your phone as well as your password.
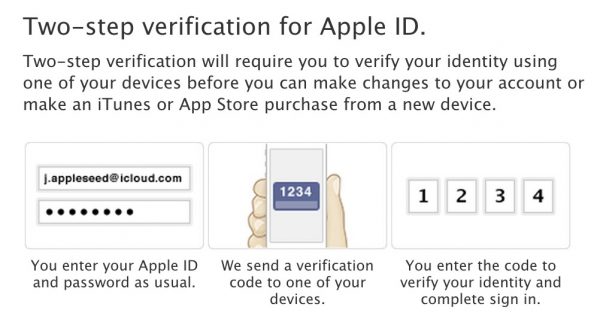
Two-step verification for Apple ID (as described by Apple)
Unfortunately, this isn’t necessarily the case – two-step verification through SMS has already been hacked. It’s a flawed system, and let’s hope a better one will come around soon. But until then, it’s still better than only using a password. At least for your most important accounts, e.g. your e-mail and any other accounts where an attacker would be able to do considerable damage.
For more on the topic, click your way through to your friendly neighborhood digital rights guardians, the Electronic Frontier Foundation. The EFF has written a series of articles on two-step verification, covering how to set it up for twelve different online accounts.







