
Phishing,Ransomware,Shadow Brokers,Vulnerabilities
On the WannaCry ransomware attack (Part 1, presumably…)
Last Friday the world was thrown smack-dab into the middle of its biggest-ever “cyber attack.” Popular as the term is, let’s stay clear of the word cyber and call it what it was: ransomware. Here’s a summary of the weekend’s events, with some background.
The Shadow Brokers make available (some of) the NSAs tools
As I covered a few weeks ago, last April a group calling themselves the Shadow Brokers released a number of (what one could call) hacker tools. These tools are commonly believed to have been developed for the National Security Agency (NSA).
Among these tools were so-called “exploits” – a means of exploiting vulnerabilities in a system. More specifically, there was an exploit called EternalBlue that targeted vulnerabilities in Windows operating systems.
Windows had released a patch for this vulnerability in March. However, as the WannaCry ransomware started making its way across the globe, it quickly became clear that the world was far from all patched up.
One reason for this was presumably that people aren’t always eager to update their machines as soon as a new patch comes out. (Dear reader: Please, oh pretty pretty please, eagerly update your machine as soon as a new patch comes out!) Another reason was that the exploit also targeted outdated systems, like for instance Windows XP, which Microsoft no longer offers security updates for.
The UK’s National Health Services among those hit the hardest
One of the most widely-reported cases was the NHS. This case also serves to illustrate how quickly WannaCry spread across networks. In an NHS statement Friday afternoon, they note that at least 16 different NHS organisations are hit. Later that evening, the BBC reported the number to be 28. Some hours later the number is estimated to have grown to more than 40.
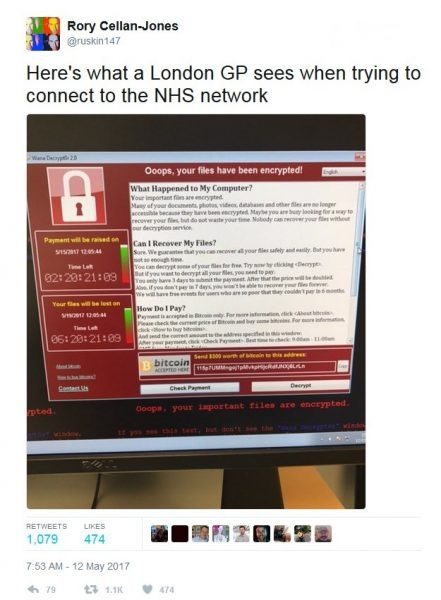
Ransomware hits the NHS (pic: Twitter user @ruskin147)
WannaCry spread through phishing
The NHS wasn’t targeted specifically: within hours WannaCry had become global. Early estimates by Kaspersky Labs (from Friday) put WannaCry’s reach at at least 45.000 computers in 74 different countries.
The attack is believed to have spread initially through phishing e-mails. An e-mail would contain a link or file which, when clicked or opened, would lead to the machine being infected.
Ransomware has been around for a while and yet this is the first instance of this kind of massive spread. The reason for this is that WannaCry was programmed to work like a computer worm. A worm is a kind of malware (from “malicious software”) that can spread automatically, replicating itself onto other computers.
All WannaCry needed was for one person to fall for the phishing. Once it was on any one single computer, it could try to infect all the other computers on the same network.
The good news: a security researcher found a “kill switch” – and Microsoft released patches for older systems
Lots of security researchers were immediately on the case. Among them was one, known only by the twitter handle @MalwareTechBlog, who noticed that once the ransomware had infected a computer, it tried to contact an obscure URL (website).
The researcher checked, and it turned out the URL wasn’t taken. He registered the domain, which resulted in the ransomware no longer encrypting files. For more technical details (and to learn what a sinkhole is), read his own write-up of the events.
Things were so bad that Microsoft decided to offer patches to protect against the outbreak – even for systems so old that they had contractually informed us that they were no longer issuing patches for them. So Windows XP, along with several other older operating systems, can (and should!) now be patched. Check out this link for more on Microsoft updates and WannaCry.
(Oh, and also – Microsoft blogged about the ransomware outbreak. Turns out they aren’t too happy with the NSA…)
The bad news: This was just the beginning
The exploits used in the ransomware attack are publicly available. And the kill switch… well, some security researchers speculate wasn’t a kill switch at all, but rather just a design flaw. Either way, similar ransomware could easily be written with a different kills switch, or none at all.
All of this is to say that we haven’t seen the last of this family of ransomware. In fact, there are already reports of copycats.
So…
What to do, what to do? Hiding under the couch won’t help. Luckily, there are other things that will. Among them:
- Watch out for phishing
- Back up your data
- Update your machines
- If you’re running an operating system that is no longer supported, switch to one that is







